Introduction
The **zkEVM prover** is a software component with which the zkEVM generates proofs that attest to correct execution of programs given a specific set of inputs.
The zkEVM prover is a software component with which the zkEVM generates proofs that attest to correct execution of programs given a specific set of inputs.
While the process of generating a proof is resource-intensive, the time required to verify the proof is significantly shorter, enabling verification to be carried out by a smart contract.
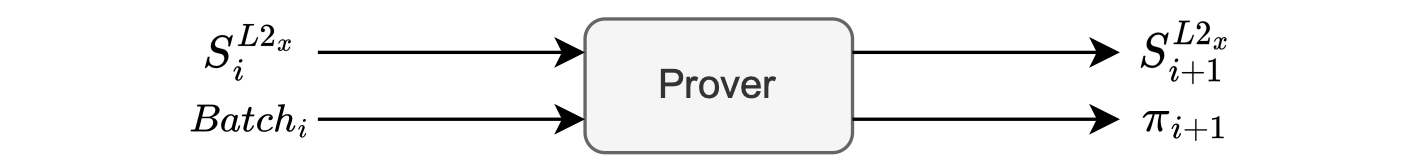
On a high level, the prover takes the last batch and the current state as inputs in order to calculate the new state, together with a proof that attests to the computational integrity of the state transition.
The figure below depicts a typical state transition ,
- Taking as inputs, a batch and the current L2 state .
- And the output as a new L2 state , together with a proof .
The initial step to produce a proof involves creation of an execution matrix, which is a matrix that records all intermediate computations constituting a larger computation. Such a matrix is also called an execution trace.
This larger computation can be thought of as the state transition function, while the smaller intermediate computations are like the zkEVM instructions or opcodes.
As we will later on see, it may take one or more zkEVM opcodes to implement a single EVM opcode.
This indicates the lack of a strict one-to-one correspondence between EVM opcodes and the Polygon zkEVM's.
Typical execution matrix
Unless otherwise stated, we use a matrix with three columns; , and .
Furthermore, suppose the number of rows is bounded by some constant , which we will call length of the execution trace.
The columns of an execution trace are often called registers. So, the terms "column" and "register" are used interchangeably in this document.
We depict an execution trace of length , having three registers , and , in the figure below.
A toy example (Execution matrix)
Suppose we are given a set of three input values, , and we want to use an execution trace to model the following computation:
Let us also suppose that the only available instructions (or operations) are those described below:
-
Copy inputs into cells of the execution trace.
-
instruction: Add two values in cells on the same row, and leave the result in the first cell of the next row.
-
instruction: Multiply a given value by a constant, and leave the result in the first cell of the next row.
-
instruction: Multiply two values in cells on the same row, and leave the result in the first cell of the next row.
Let’s provide a specific example by setting the input to .
Substituting the input values in the given computation yields:
The corresponding execution trace, using only the above-mentioned operations, is as follows:
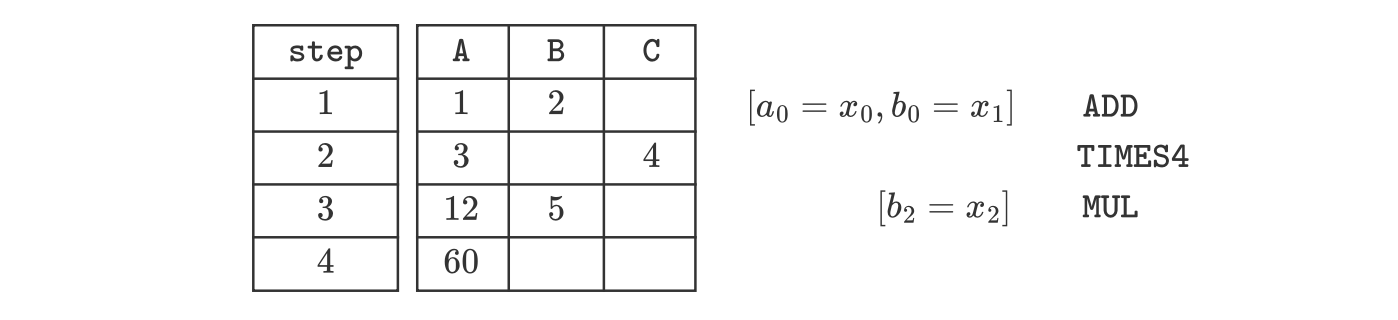
Let’s take a step-by-step walk-through the above execution trace:
- First of all, we use the instruction that copies the inputs and into the columns and , respectively. And then invoke the instruction.
- After executing the instruction, the second row of register now holds the sum of and , that is the value . At this point we utilize the instruction to obtain , and place it in the first cell of row 3.
- Now, with in the third row of register , we proceed to copy the third input, , into register . Then the instruction is invoked to multiply the current two values in row 3. (viz. and ). The resulting outcome (which is ) of the instruction is placed in the first cell of row 4.
- Consequently, this last outcome is in fact the final output for the entire computation.
Observe that we have only used the available instructions as proposed in our scenario.
Notice that for a specific computation, and except for the entries in the matrix, the shape of the execution matrix remains the same irrespective of the variable input values .
For example, if for the same program, the resulting execution matrix is as follows:
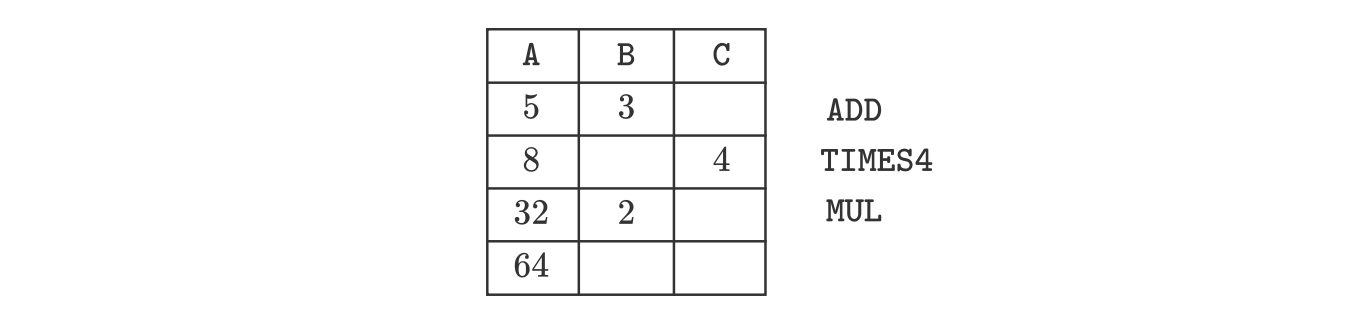
However, if we examine the columns in the above execution trace, we can identify two distinct types of columns:
- Witness columns: Values in these columns depend on the input values. They change whenever different input values are used. In the above example, columns and are witness columns.
- Fixed columns: Values in these columns remain unaffected by changes in the input values. In the above example, column is a fixed column, and it is only used to store the constant .
In each case of the above example, the constant is used in the second step of the computation, when the instruction is invoked.
Last updated on
How rollbacks work
Recall that the server-source protocol begins with calling the $ exttt ( )$, corresponding to which a message is sent to the stream server, preparing to recei
Executor
The executor is responsible for generating a correct execution trace from a given set of inputs. As shown in the figure below, the executor takes some inputs an